- Advertising
- Bare Metal
- Bare Metal Cloud
- Benchmarks
- Big Data Benchmarks
- Big Data Experts Interviews
- Big Data Technologies
- Big Data Use Cases
- Big Data Week
- Cloud
- Data Lake as a Service
- Databases
- Dedicated Servers
- Disaster Recovery
- Features
- Fun
- GoTech World
- Hadoop
- Healthcare
- Industry Standards
- Insurance
- Linux
- News
- NoSQL
- Online Retail
- People of Bigstep
- Performance for Big Data Apps
- Press
- Press Corner
- Security
- Tech Trends
- Tutorial
- What is Big Data
How to protect your cPanel server from DDoS attacks
Distributed Denial of Services attacks, or DDoS as they are commonly known as, are among the most common threats that can take a website or even an entire server offline. A present-day system administrator is expected not only to handle hardware or software issues, but also to have solid security skills and to be able to protect servers from attacks. If you administer your own WHM server, you will also benefit from the below article, in which we explore some simple methods to avoid downtime, using the free tools available in the WHM/cPanel hosting platform.

First things first...
What is a DDoS attack?
The ancestor of the DDoS attack was the simpler Denial of Service (DoS) attack. A DoS attack tries to saturate a server by sending a large number of requests that use all available connections and make the service inaccessible for legitimate users.
However, DoS attacks were easy to stop because they originated from a single IP address. A system administrator could simply block it and the attack was over.
DDoS attacks follow the same principle, but they are launched from a botnet of infected machines. These can be any kind of equipment connected to the Internet, from servers or home computers to security cameras or other IoT devices.
Since the requests come from hundreds or thousands of different IP addresses, from all around the world, it is very difficult to identify which requests are malicious, or to manually block them all.
Types of DDoS attacks
There are various types of DDoS attacks, that can target every of the 7 network layers defined by the OSI model.
For example, a Layer 4 (Transport layer) attack targets the TCP protocol, while a Layer 7 (Application layer) attack tries to overwhelm the applications.
Amplification attacks are even more dangerous since vulnerable online services (such as open NTP or DNS servers) are used to increase the size of the requests. This type of attack was used in some of the most massive DDoS attacks in history.
How to block DDoS attacks
The easiest way to protect a server from DDoS attacks is to use an external service, such as Cloudflare. Even the free tier of Cloudflare includes basic DDoS protection, with more sophisticated mechanisms available in the paid plans.
However, there are cases when external services can’t be used, for various reasons. Let’s see how the tools already available in WHM can limit the effect of a DDoS attack on the server.
Apache mod_evasive
Mod_evasive is a module available for the Apache HTTP server that can automatically block attacks by rate-limiting any IP that sends too many requests in a short time.
Start by installing the module from WHM’s EasyApache 4 interface. Select the Currently Installed Packages profile, search for mod_evasive in the Apache Modules section, and then install it.
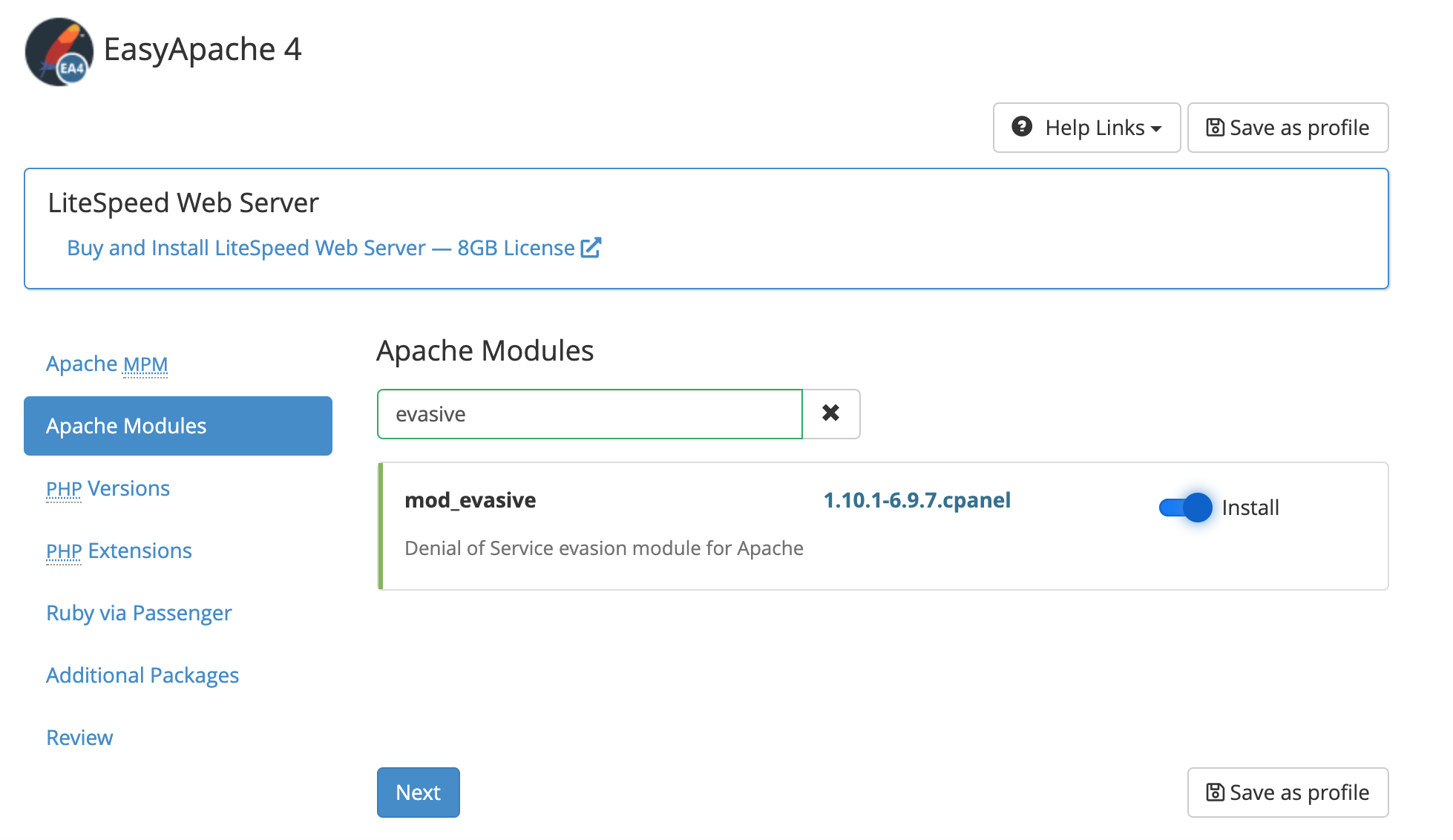 The default settings are good for most servers, but you can tweak them further by editing the configuration file /etc/apache2/conf.d/300-mod_evasive.conf. You can also whitelist specific IP addresses or classes, so legitimate requests are not blocked.
The default settings are good for most servers, but you can tweak them further by editing the configuration file /etc/apache2/conf.d/300-mod_evasive.conf. You can also whitelist specific IP addresses or classes, so legitimate requests are not blocked.
Configure CSF to block attacks
While mod_evasive works very well, it only protects the Apache webserver. In order to harden other services as well, you can install the free ConfigServer Security & Firewall (CSF), which also includes a WHM plugin.
As the root user, install CSF with these terminal commands:
cd /usr/src rm -fv csf.tgz wget https://download.configserver.com/csf.tgz tar -xzf csf.tgz cd csf && ./install.sh
The WHM plugin interface is found in Home >> Plugins >> ConfigServer & Firewall.
CSF is a very complex and powerful firewall, with many options. A detailed configuration walkthrough is outside of the scope of this article, but let’s see which CSF features can stop a DDoS attack.
Click on the csf tab and then scroll down and click on Firewall Configuration.
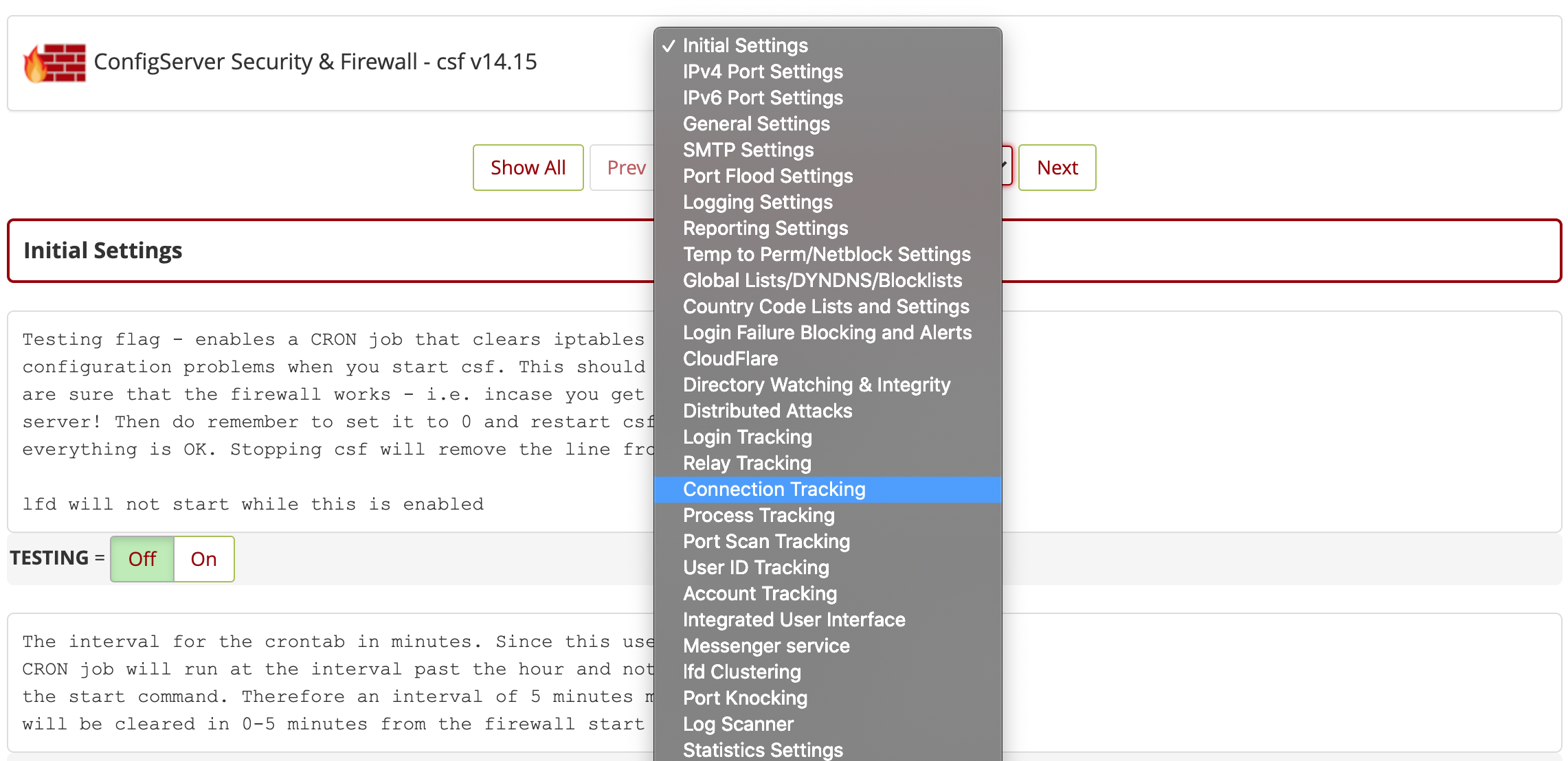
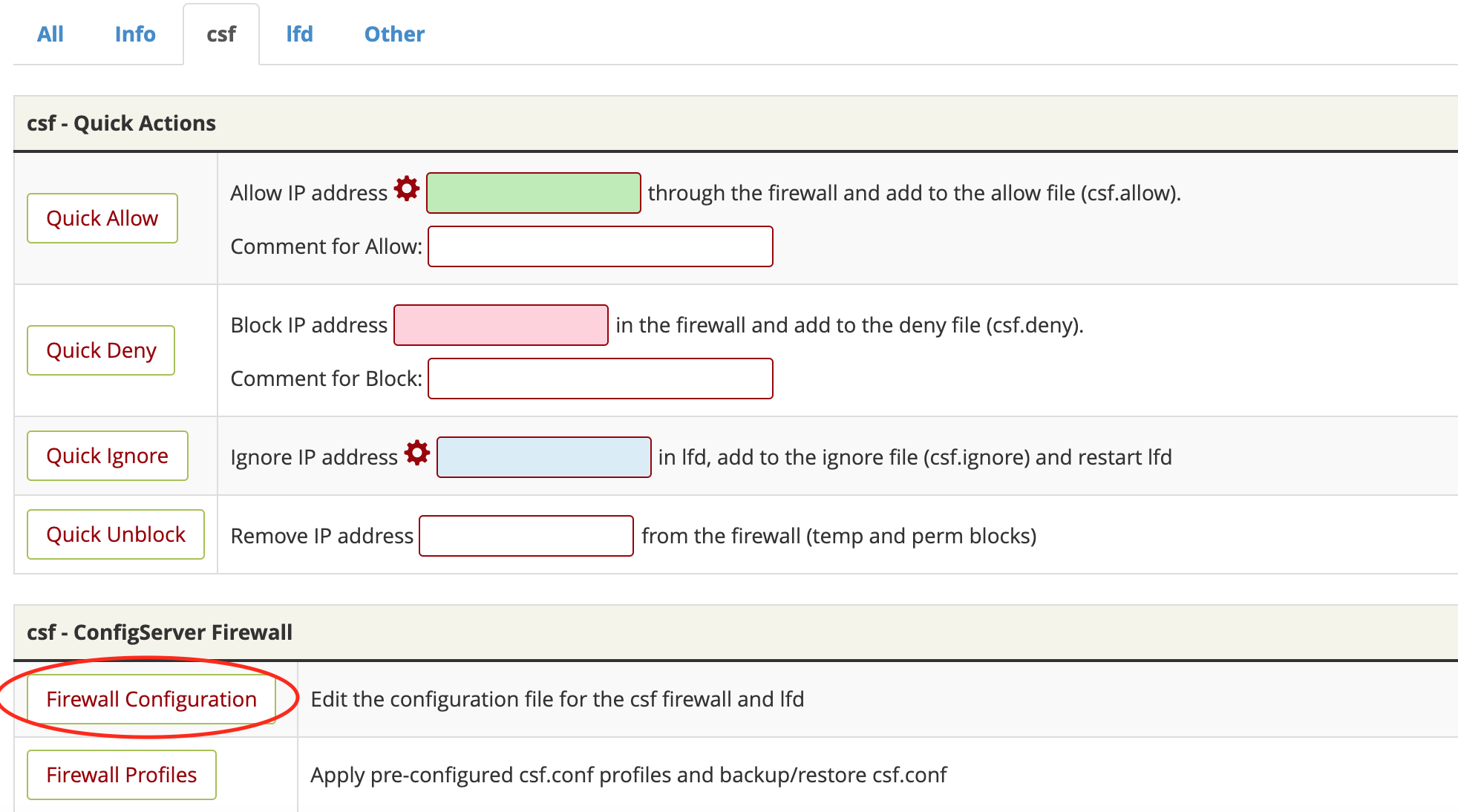 From the drop-down menu, select Connection Tracking.
From the drop-down menu, select Connection Tracking.
 The CT_LIMIT value sets a maximum limit of connections allowed from a single IP address, while CT_INTERVAL sets the number of seconds between scans.
The CT_LIMIT value sets a maximum limit of connections allowed from a single IP address, while CT_INTERVAL sets the number of seconds between scans.
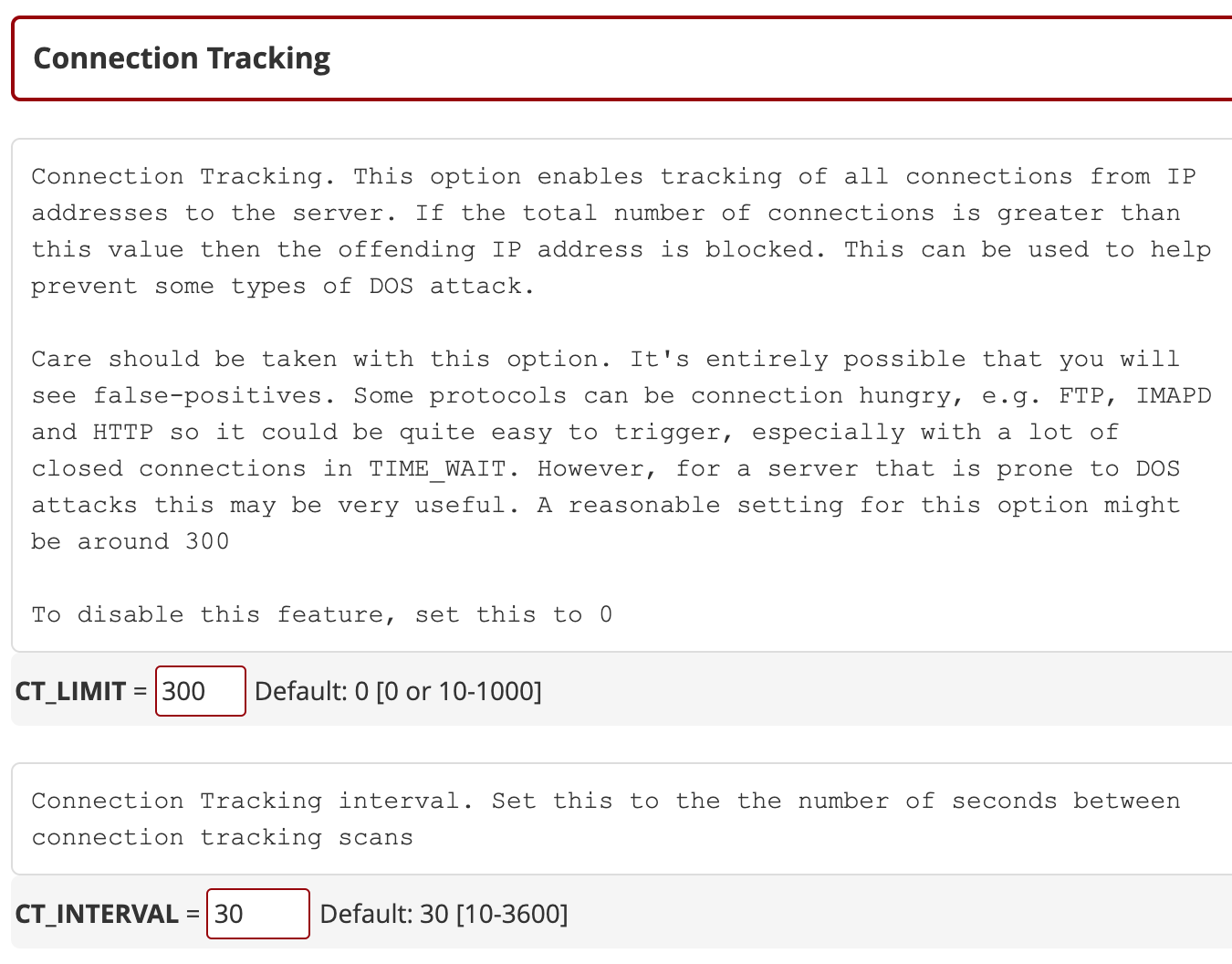 There are many other settings that you can tweak here, for example CT_BLOCK_TIME controls the temporary ban duration (in seconds) for offending IPs.
There are many other settings that you can tweak here, for example CT_BLOCK_TIME controls the temporary ban duration (in seconds) for offending IPs.
Additional anti-DDoS mechanisms can be configured in the Port Scan Tracking section, such as Syn Flood Protection (a Layer 4 attack). You can also define custom rules for specific ports (check the CSF documentation for the correct syntax).
Why correct settings matter
Improper settings can cause legitimate users to be banned or cause significant server load or network latency. It is a good idea to start with the default values and adjust them as needed.
Please also keep in mind that even the best protected websites in the world can still be vulnerable to a well-orchestrated DDoS attack. However, the steps described in this article can offer decent protection to a WHM server and limit the damage done by normal attacks.
If your server still struggles to stay online and you need additional advice, leave a comment below, contact us, or opt for our managed services package.
Readers also enjoyed:

cPanel & WHM: Learn the Difference on Bigstep Metal Cloud


Leave a Reply
Your email address will not be published.