- Advertising
- Bare Metal
- Bare Metal Cloud
- Benchmarks
- Big Data Benchmarks
- Big Data Experts Interviews
- Big Data Technologies
- Big Data Use Cases
- Big Data Week
- Cloud
- Data Lake as a Service
- Databases
- Dedicated Servers
- Disaster Recovery
- Features
- Fun
- GoTech World
- Hadoop
- Healthcare
- Industry Standards
- Insurance
- Linux
- News
- NoSQL
- Online Retail
- People of Bigstep
- Performance for Big Data Apps
- Press
- Press Corner
- Security
- Tech Trends
- Tutorial
- What is Big Data
GDPR and Big Data in the Cloud
Many of our customers have asked about how will GDPR affect our commercial or technical relationship. Since we host a lot of “personal data” on our servers, that makes us “data processors.” I will try to give more clarity on this subject.

Many of our customers have asked about how will GDPR affect our commercial or technical relationship. Since we host a lot of “personal data” on our servers, that makes us “data processors.” I will try to give more clarity on this subject.
The short answer is that it is nothing to worry about and that we can help.
There is a whole host of information out there describing GDPR in far more detail than I could ever get into, but I think a summary is in order:
GDPR crash course
This regulation introduces new “human rights” and new “obligations” for companies that control what happens with the end consumer’s data. To be precise, some of these are not exactly new, but the terms have been better defined, or their meaning expanded.
A. New and updated human rights (any human will have the right to ask the company he buys something from the following):
1. RIGHT OF ACCESS (Article 15)
“explain what you do with my data (esp. profiling)”
“let me choose what I allow you to do with my data.”
“tell me what data you have on me right now.“
“give me the data that you have on me.”
2. RIGHT TO BE FORGOTTEN (Article 17)
“delete my data from your servers.”
3. RIGHT TO DATA PORTABILITY (Article 20)
“move my personal data to this other vendor.“
B. New obligations for companies (any company dealing with personal data must):
1. OBLIGATION TO IMPLEMENT PRIVACY BY DESIGN (Article 25 & 32)
build & architect with security and privacy in mind from the start.
2. OBLIGATION TO REPORT DATA BREACHES (Article 33 &34)
report incidents to the authorities
3. OBLIGATION TO PERFORM DATA PROTECTION IMPACT ASSESSMENTS (Article 35)
have a well-documented study of what happens to data in the company
4. OBLIGATION TO APPOINT DATA PROTECTION OFFICERS (Article 37)
have somebody in charge of actively protecting “data subject's" interests
There are many exceptions from these rights and obligations. They also have broad implications that might not be obvious from the start. For instance, the 1st obligation implies that when a company designs an algorithm, it should be done in such a way as to protect vulnerable categories of people such as women or immigrants from algorithmic discrimination.
My personal opinion is that you should try to understand the concepts behind the GDPR’s rules, the “spirit of the law” if you want. I think the reasoning is quite simple, but the implementation’s complexity is due to the nature of the field they are trying to regulate.
Some people feel the rules are rather complicated or vague at times. I’m afraid there is simply no easy and clear-cut way to both protect “data subjects” and enable businesses to function.
Our relationship with you as our client and with your end user.
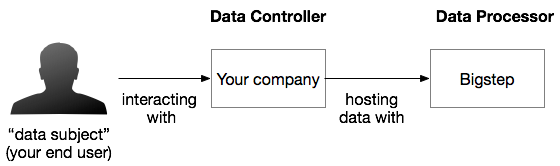
From the GDPR’s perspective, Bigstep is a data processor for the end-users PII data. In a simple scenario, if you “determine the purposes and means of the processing of personal data” on the “data subjects,” i.e. your end users’ data, you will be the Data Controller.
If you are for instance a Data analytics SaaS company hosting data with us but also providing your services to a third-party company that in turn provides services the end user then you are a Data Processor too.
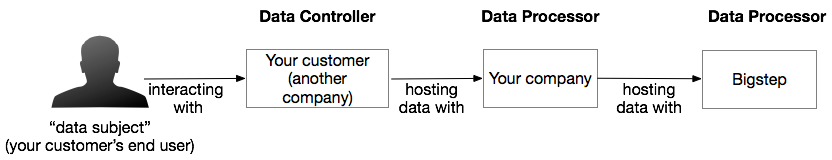
In all situations, Bigstep is a Data Processor for you even if we are storing encrypted data and virtually no “processing” takes place. Data Processors and Data Controllers have different obligations under GDPR and figuring out which one is you is important.
Our obligations to you under GDPR
In broad terms, as Data Processors we are obligated to:
Obey your instructions on how to handle your data. Processors are required to process personal data by the controller's instructions. This is a broad definition which in effect imposes an indirect obligation to obey many of the obligations that you as controller have albeit at your instruction.
How we do it:
For self-managed customers, we do not touch your data unless in an automated fashion and only if you as a user using our UI or API to instruct our systems to interact with your data. In effect, all your data is very much under your control.
For Single Point of Contact customers, we design a “Solution” document at the start of our business relationship. Typically, that is during the Proof of Concept phase. That “Solution” document is the sole description of our access and handling right. We design your infrastructure and handle the data only in the scope of that solution. Anything outside of it will be subject to your approval. For instance, we will not be removing data from your infrastructure as the recipient systems would not be part of the “solution” effectively isolating your data to your pre-defined set of servers and actions.
Apply the Privacy by Design principle.
This means we need to make sure we architect our products from the get-go so that they are as safe as they can be with the current technologies.
How we do it:
Our architecture is very new, less than four years old and designed in an era with modern security threats, Intel CPU vulnerabilities and others and the fact that we use bare metal when all other clouds use virtual machines is a testament to that. We believe in isolating customer’s machines physically from one another. We are also the only ones that create L2 overlay networks on physical switches rather than L3 on virtual ones. These were design decisions taken with security and performance in mind.
The solutions that we build for you will also be designed with security and privacy in mind, and we will voice our concerns if you choose to go for a less secure route.
Not transfer data in other countries if safeguards are not in place
Regardless of specific instructions from you as Controller, we still need to make sure the country in which data is transferred is deemed safe.
How we do it:
We never transfer data outside of the datacenter that the customer has chosen the data to reside hence outside a country unless explicitly instructed by you. We will only transfer data within our data-centers. In the unlikely event that you instruct us to transfer data to a third party in a country that we do not consider safe, we might refuse.
Report Data Breaches to you
As data processors, we need to notify you of a data breach that affected your servers. It is your decision how to handle that incident afterward. More information on this can be found here.
How we do it:
We never had any breaches that affected customers other than self-service customers configuring crackable ssh passwords on their servers. Should we ever have a data breach due to Bigstep, we will notify all our affected customers immediately.
Get your consent when subcontracting
We need to get your consent if your data ever reaches a 3rd party.
How we do it:
We do not currently use any third-party service to host data other than colocation providers which only provide the racks and power which we require to be Tier-4 certified.
Demonstrate compliance
Should you require, we need to be able to demonstrate that we are compliant. This means we need to maintain a record of all categories of processing activities or details of transfers of data to other countries.
How we do it:
Our compliance will also be verified by a certification as soon as one is available. In the meantime, we will use our self-assessment and all our other certifications as means to prove compliance.
You can always submit a request for details on compliance stating the exact area of interest and your data processing intent. You will be able to use that document as part of your documentation regarding your vendors. That documentation is important because if the event of a data breach you can use it to demonstrate that you work with a reliable partner (us).
Appoint a Data Protection Officer
The DPO is the person(s) that oversees our GDPR compliance and is responsible for making sure we respect our fellow citizens.
How we do it:
Our DPO is an independent contractor with whom we have worked for many years. You can submit requests at dpo@bigstep.com at any time.
Have a contractual relationship with GDPR
The binding obligations on the processor (us) must cover the duration, nature, and purpose of the processing, the types of data processed and the obligations and rights of the controller.
How we do it:
The terms of use and conditions that you have signed (digitally or otherwise) include provisions to govern this relationship. However, they do not cover everything, and we will be contacting you to sign some addendum to them where necessary. We do not expect any commercial conditions to change.
Conclusion
There is much effort involved in keeping our end-user protected. As a Big Data company, our work touches the data of millions of people. Often, a secure system is a far less flexible system. However, all this effort ultimately adds up to a safer, better society in this digital age and I believe it is worth it.
Disclaimer: This is not a legally binding document. Seek professional advice. Contact dpo@bigstep.com for more information.
Leave a Reply
Your email address will not be published.