- Advertising
- Bare Metal
- Bare Metal Cloud
- Benchmarks
- Big Data Benchmarks
- Big Data Experts Interviews
- Big Data Technologies
- Big Data Use Cases
- Big Data Week
- Cloud
- Data Lake as a Service
- Databases
- Dedicated Servers
- Disaster Recovery
- Features
- Fun
- GoTech World
- Hadoop
- Healthcare
- Industry Standards
- Insurance
- Linux
- News
- NoSQL
- Online Retail
- People of Bigstep
- Performance for Big Data Apps
- Press
- Press Corner
- Security
- Tech Trends
- Tutorial
- What is Big Data
Five Ways to Secure a CentOS 8 Server
The latest version of the CentOS operating system comes with robust security features. However, not all of them are active or properly configured by default, so a new installation is vulnerable to hacks and intrusion attacks. Since one of the most important tasks of a modern system administrator is security, let’s review a few simple steps than can greatly harden the security of a CentOS 8 server.

Set Up A Firewall
Configuring the firewall is usually the first security task on a fresh installation, in order to allow traffic only for specific services and ports. The default firewall on CentOS systems is firewalld, you can start and enable the service with the following commands:
systemctl start firewalld systemctl enable firewalld
Firewalld configuration is outside the scope of this article, but the commands are simple and intuitive. Allow access only for trusted IP addresses and open only the ports required by the services that run on the server.
If you wish, you can also choose an alternative firewall solution that offers enhanced features, such as CSF.
Secure SSH
The SSH service is one of the most targeted by hackers, especially when running on the well-known default port 22. You should change it to a random one, so edit the configuration file of the secure shell server:
vi /etc/ssh/sshd.config
You will notice that the line that sets up the port is commented out, so add a new one with a port between 10000 and 60000 (in this example, 22212), then save and close the file:
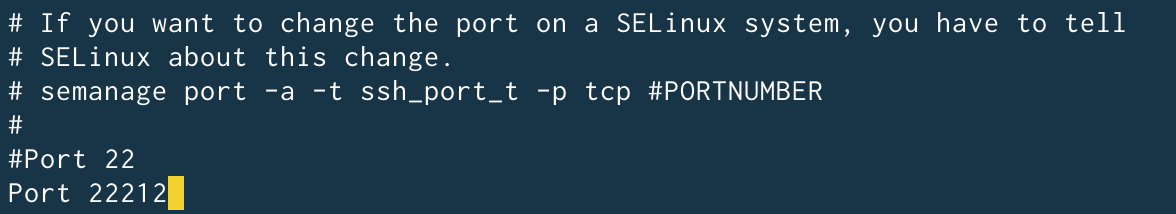
If SELinux is active on the server, also run the following command in order to modify its default policy, and then restart the sshd service:
semanage port -a -t ssh_port_t -p tcp 22212 systemctl restart sshd
It will now listen to a port that is rarely subjected to brute force attacks. For additional security, consider disabling password authentication completely and setting up pairs of ssh keys for remote logins.
Keep Your System Up to Date
Updating packages can greatly reduce the risks for your server, since new versions patch known security vulnerabilities and exploits. It is possible to set up CentOS 8 to update automatically, but this might not be desired. Sometimes, updated packages can disrupt the functionality of critical services, so it is a good idea to update manually and test sensitive updates before applying them.
Updating is easy from the command line, using either the old yum or the new dnf package management tool:
dnf update
Restart your server periodically when activity is low, in order to load new kernel versions.
Disable Unused Services
CentOS 8 comes with a number of services active by default, some of which you might not use. These should be disabled, since each one is a potential security risk. For example, the Postfix mail server is active and listens for connections on port 25. If you don’t need this service, stop and disable it. You can also uninstall Postfix from your server:
systemctl stop postfix systemctl disable postfix dnf remove postfix
Active services can be identified in several ways, for example using the systemctl command:
systemctl list-unit-files
To inspect active listening ports, use the ss command locally or scan your server from another machine with nmap:
ss -tulpn
Enable SELinux
SELinux is a kernel security module that is quite controversial in the Linux community. It offers a solid set of access control policies but can be difficult to configure, so some system administrators disable it on all installations. Since the additional security layer provided is very useful, make sure that SELinux is enforced on your server.
Check if the service is active with the sestatus command:
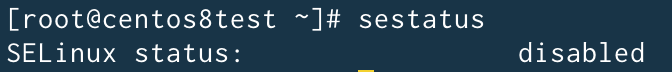
If SELinux is disabled it cannot be enabled without rebooting. Edit its configuration file with your favorite text editor and change its state from disabled to enforcing:
vi /etc/sysconfig/selinux
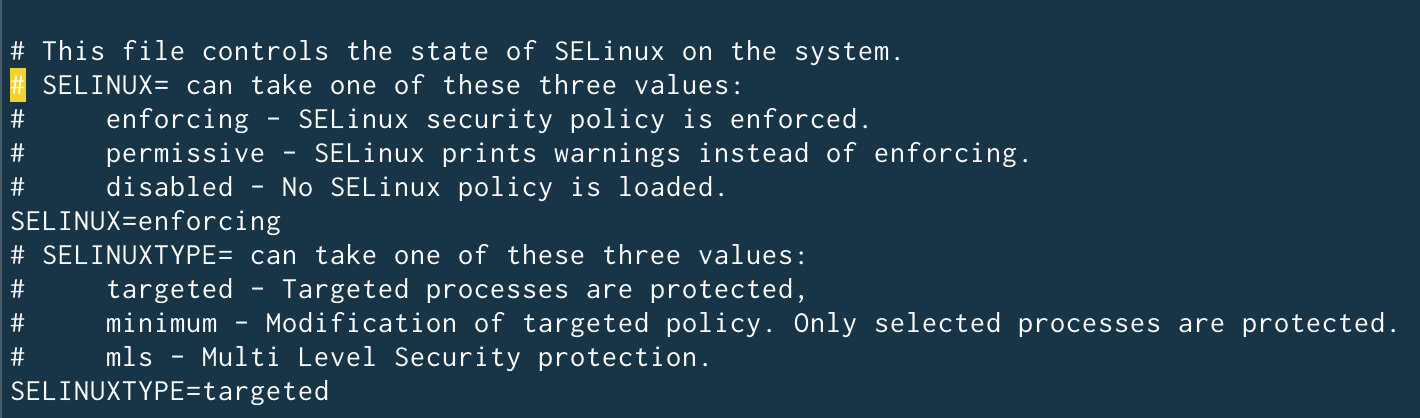
The service will be enabled after the next restart. If you are not familiar with its configuration, you should choose the permissive mode initially, which will only log policy violations and allow you to understand how it works.
Managing server security is a very complex task and no machine is ever fully safe, even with the perfect settings in place. However, implementing the steps described in this short tutorial will greatly harden your security on CentOS 8. If you have any questions about any of the steps, or about server infrastructure, we’re here to help.
About the Author
Dragos Baldescu is a Level 2 Technical Support Engineer at Bigstep, passionate about Linux and testing out new technologies and solutions.
Readers also enjoyed:
Five Essential Apps To Install On A Fresh CentOS 7 Server


Leave a Reply
Your email address will not be published.